Q: I want to use my own TLS certificate when connecting my INSTAR WQHD camera to my Mosquitto 2 broker. But because I only use a local domain I cannot use a service like Let's Encrypt to generate it. Is it possible to generate my own CA certificate?
A: Yes, but you don't have to! You camera uses an authorized certificate for it's INSTAR DDNS address. If you deactivate the Verify Certificate option in your camera's MQTT menu you can start using this certificate to encrypt the communication between your camera and Mosquitto broker. To be able to leave the certificate verification active, you would need to have some local DNS server (or an edited hosts file on each computer) that resolves your cameras DDNS address to it's local IP address. You can add your cameras CA Root certificate to your broker configuration as the cafile. Details on how to download this certificate can be found in the CA Custom Store article.
If you really, really, REALLY want to use your own certificate you can Take Matters into your own Hands and generate it yourself. Once you walked through all those steps return here to use the generated file in your Mosquitto configuration.
Mosquitto Server Configuration
Now we need to add the ca.crt, server.crt and server.key to our configuration file /etc/mosquitto/conf.d/custom.conf:
# -----------------------------------------------------------------
# Certificate based SSL/TLS support
# -----------------------------------------------------------------
listener 8883
tls_version tlsv1.2
cafile /etc/mosquitto/certs/ca.crt
certfile /etc/mosquitto/certs/server.crt
keyfile /etc/mosquitto/certs/server.keyNote: INSTAR Full HD Camera require tlsv1.2 while INSTAR WQHD Cameras use the newer tlsv1.3. You can replace the
tlsv1.2configuration with atlsv1.3if you only work with WQHD Cameras.
Then restart the service:
service mosquitto restart && service mosquitto statusTesting the Connection
All you need to establish a server connection is the ca.crt file on your client machine. Then you can try to subscribe to the last-will topic of your camera and should receive it's online status:
mosquitto_sub -h debian11 -t 'cameras/117/status/connection' -p 8883 --insecure --cafile ca.crt --tls-version tlsv1.2 -u admin -P instar -v
cameras/117/status/connection {"val":"online"}
cameras/117/status/connection {"val":"offline"}
cameras/117/status/connection {"val":"online"}Note the --insecure flag in the subscription above. If everything went right while generating the certificates you should be able to remove it and still connect successfully.
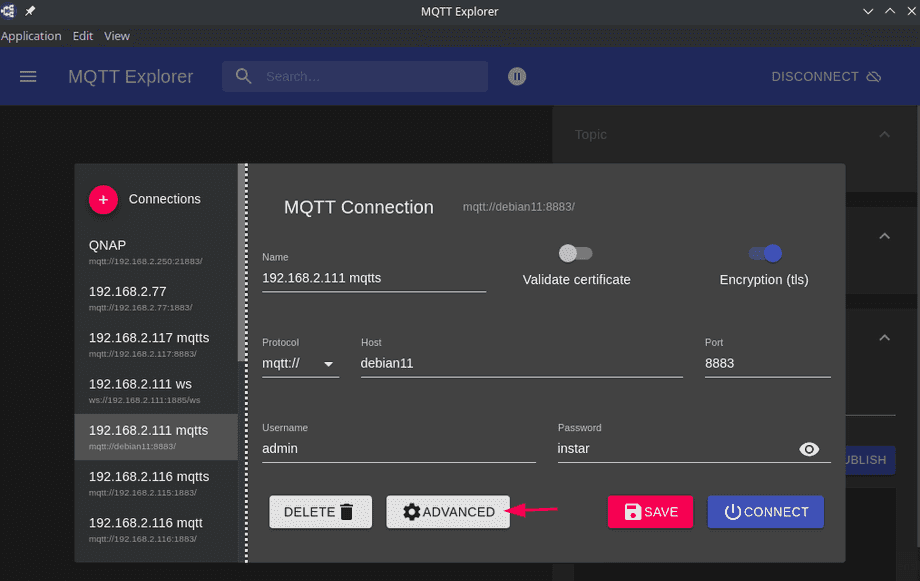
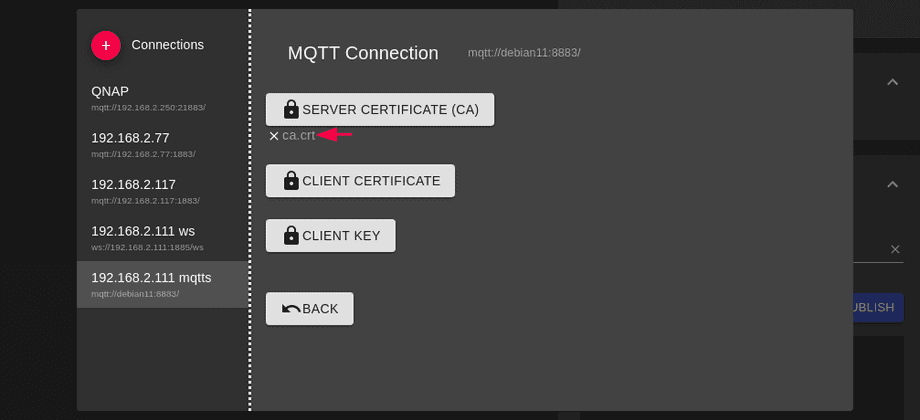
Or with the MQTT Explorer - again we start with the Certificate Verification deactivated. Type in the connection details and click on Advanced to add the cafile:
Click on connect - if it works try activating Validate Certificate option.